The contactless IC card module consists of a non-contact IC card reader chip FM1702 and its peripheral circuits. Second, FM1702 chip functional block diagram and pin diagram Third, the flow chart of the operation of the non-contact IC card is as follows: After power-on, first use the program to initialize the register of the card reader chip (hereinafter referred to as PCD), and then enter the card-seeking state after completion, and issue a card-seeking signal through the antenna. When there is an IC card (hereinafter referred to as PICC, the card used in the experimental program is the MF1 S50 card) enters the effective operation area of ​​the antenna, and after receiving energy, it returns to the PCD card type value. In the next step, the PCD performs a collision operation on the card. After the PICC obtains the anti-collision operation signal, it returns to the PCD card serial number. After the PCD receives the serial number, the program determines the validity of the serial number. After confirming that the PICC serial number is valid, the PCD sends a card selection command, and the card selection includes sending the selected card serial number, so that the card for the next operation is unique. The PCD loads the key. The key is the same as the PICC sector key to be operated. The same fan has two sets of keys, keys A and B. If the A key is authenticated, the key is the A key. For the B key authentication, the B key is required. After the key is successfully loaded, the authentication operation is started three times. The certification process is carried out like this: Fifth, the basic test method of the module
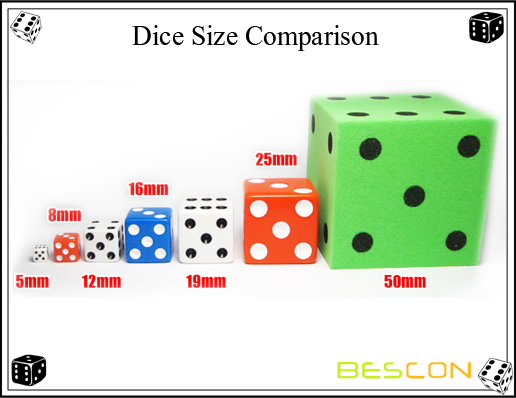
The 25MM (1 inch) dices are solid, hefty dice, perfect for party or casino games, classroom use, or decorative purposes. If you need dice that are readable from a few feet away, these do the trick.
With all the sizes of dice available, don't know which size you need? Is a 12MM Dice big enough to easily game with? Just how large is a 25mm dice compared to other game components? Take a look below at our examples of all the common dice dimensions to find out!
25MM Dice Big,Big Dice for Sale,Large 6 Sided Dice,Oversized Dice Wholesale BESCON INDUSTRIAL CO., LIMITED , http://www.besconcn.com
First, FM1702 chip introduction
The FM17XX series is a series of non-contact card readers based on the ISO14443 standard designed by Fudan Microelectronics Co., Ltd., which adopts 0.6 micron CMOS EEPROM technology and can support three types of typeA, typeB and 15693 at 13.56MHz respectively. The communication protocol supports the MIFARE and SH standard encryption algorithms and is compatible with Philips' RC500, RC530, RC531, and RC632 card reader chips. The chip is highly integrated with an analog modem circuit that works with a minimum of peripheral circuitry. Supports 6 kinds of microprocessor interfaces. The digital circuit has two voltage working modes, TTL and CMOS, which are suitable for the application of card readers of various billing systems.
1, product features
â—Highly integrated analog circuit requires only a minimum of peripheral lines â— Operating distance up to 10cm
â—Support ISO14443 typeA typeB 15693 protocol â—Include 512byte EEPROM
â— Supports MIFARE and SH standard encryption algorithms â— Supports six interface modes â— Contains 64byte FIFO
â— Digital circuit has TTL/CMOS voltage working mode â— Software controlled power down mode â— One programmable timer â— One interrupt processor â— One serial output input port â— Start configuration programmable â— Digital analog and transmit modules have Independent power supply â— SOP32 package â— FM17XXL version means that the chip's three power supplies are suitable for low voltage
2, the difference between the models: .jpg)
.jpg)
.jpg)
The following figure shows the block diagram of the token for three-pass authentication: .jpg)
(A) ring: a random data RB is sent to the reader by the Mifare 1 card;
(B) ring: after receiving the RB by the reader, send a token data TOKEN AB to the Mifare 1 card, which contains a random data RA sent by the reader;
(C) Ring: After receiving the TOKEN AB, the Mifare 1 card decrypts the encrypted portion of TOKEN AB and verifies whether the random number RB sent by the Mifare 1 card in the (A) ring is the first time (B) The RBs in the TOKEN AB received in the ring are consistent;
(D) Ring: If the (C) ring check is correct, the Mifare 1 card sends the token TOKENBA to the reader to the reader;
(E) Ring: After the reader receives the token TOKEN BA, the reader will decrypt the RB (random number) in the token TOKEN BA; and verify the first time by the (B) ring reader Whether the outgoing random number RA is consistent with the RA in the TOKEN BA received in the (D) ring;
If each of the above rings is "true" and can pass the verification correctly, the entire authentication process will succeed. The reader will be able to proceed to the next step (READ/WRITE, etc.) for this sector on the card that has just been authenticated.
Other sectors in the card cannot be further manipulated because they have their own passwords. If you want to operate on other sectors, you must complete the above certification process. Any part of the certification process will be wrong and the entire certification will fail. Must start from scratch. If the password on the card is not known in advance, the change in the password can be extremely complicated, so the possibility of opening a sector on the card by guessing the password is almost zero.
Here to remind programmers and card users, you must keep in mind every password in the 16 sectors of the card, otherwise, forgetting the password of a certain sector will make the data in the sector unreadable. There is no way to save this low-level mistake. However, other sectors on the card can be used as they are.
The above description can fully explain the high security, confidentiality, and card application diversity of the Mifare 1 card, and one card multi-purpose (one card).
For detailed operation, refer to the FM1702 manual, MF1 S50 manual, and 14443 protocol.
Fourth, the circuit schematic .jpg)
Use the jumper cap to short-circuit the CS0 of the module, and select Mode_Select to select the independent mode. That is, ALE, A0, A1, and A2 are short-hopped and all are connected to the Separate end. The REST of the module is connected to the P+ of the experiment box.
Insert the module into the expansion slot of the single-chip experimental box, power on, and open the file: Hardware.asm. Compile and debug, discard the breakpoint according to the comments in the program, run the program, and observe the contents of the first three breakpoints in turn.
At the first breakpoint, the contents of the 30H-5FH unit are all: 0FFH.
At the second breakpoint, the A content is 4, which is normal.
At the third breakpoint, the content of the 39H-3CH unit changes, which is the serial number of the card reader chip. The serial number of each card reader chip is different.
At the fourth breakpoint, the right end of L1, L2 is measured with a sine wave with a peak-to-peak value of about 7V, and the L1 and L2 waveforms are reversed; the right end of C3, C5 has a sine wave with a peak-to-peak value of about 3.5V, and the waveform is reversed; At the right end of C12 and C13, there is a sine wave with a peak-to-peak value of about 7V, and the waveform is reversed. For example, if the ground end of the oscilloscope probe is connected to the detecting end and the ring is equal in size to the antenna coil, the ring is placed on the top of the antenna and close to the circuit board, so that a sine wave with a peak-to-peak value of about 2.5V can be sensed. The first three breakpoints are correct, indicating that the register access is normal. At the fourth breakpoint, the measured data is normal module data.
Remove the breakpoints 1, 2, 3. Leave breakpoint 4 and set breakpoints 5, 6. Debug M1 card (MF1 S50 card). Run the program from breakpoint 4, place the card about 4 cm above the antenna coil of the card reader module, and repeatedly execute the program to observe whether the value of A or R6 at the breakpoint 5 is normal, and the position of the card above the antenna does not change. If it is normal, continue to execute the program, go to the breakpoint 6 and observe 30H, 31H content is: 04H, 00H. The card search is valid. The module can operate the card normally. The program can be run repeatedly to observe the effective distance change to the card operation.