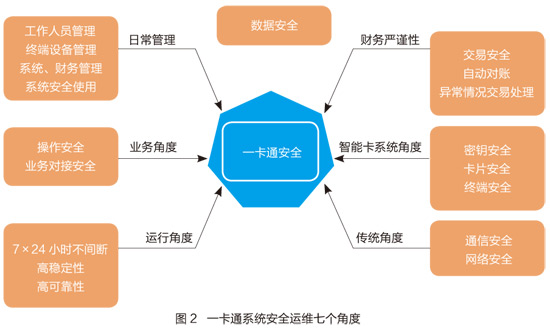
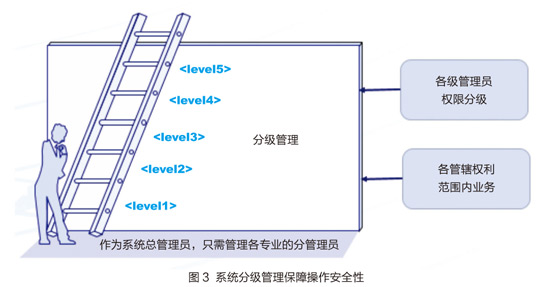
The campus card system involves many aspects of campus life and is summarized into three categories: consumer, financial, and identity. These three categories cover most applications, as shown in Figure 1. In addition to the front-end applications, the operation of the card is inseparable from the back-end infrastructure and hardware support. The associated network and terminal hardware are also very large, all over the campus, and closely related to the life of each teacher and student. . With the development of technology, the status and importance of the card in the digital campus is increasing day by day, and its security issues are widely related. It is a problem that needs long-term discussion and long-term prevention. There are many applications for cards, and there are many security factors. The following is a comprehensive analysis of the security factors of the card system from different angles, as shown in Figure 2. Traditional perspective: communication security, network security From a traditional point of view, the security of the card system should consider its communication security and network security; the campus card system is a financial consumption system, which is related to money. For security reasons, the campus card network must be a private network. It usually consists of two parts, one is the TCP/IP backbone network, and the other is the LAN of the 485 protocol. Each part involves network security issues. Traditional network security issues: firewalls, security policies, etc. This article does not discuss in depth. Backbone network security issues: For the one-card network, some universities are dedicated physical networks, and some universities are separated by a VLAN network of campus networks. The purpose of this is to ensure communication and network security. The main object of card network access is a card-related device, and the network environment is relatively simple. However, there is a drawback. The network ports are distributed throughout the public buildings of the campus. It is impossible for a dedicated person to be on duty. Deliberate vandals can access the card network, and there are security risks such as posing as a gateway and spreading viruses. LAN security issues: 1. All-in-one consumer POS equipment, identification equipment and other access networks are 485 protocol LAN, such as the POS machine LAN of the cafeteria. Its potential security problem is mainly the high temperature and high humidity of the network line itself, which easily leads to the aging of the network line. , affecting communication. 2. The communication gateway of the local area network is also a security risk point that often fails. Because the weak electricity room is in a high temperature and high humidity environment, and there is no refrigeration equipment, especially in the summer, the ambient temperature is too high, the heat is not timely, and the gateway equipment that has been working is prone to crash and damage, resulting in Communication is interrupted. Business perspective: business operation security, business connection security One card is an application system, and it is also playing the role of an identity access platform, and its business involves a wide range. Business operation security: The business operations involved in the card include: card operation window staff daily operations including card initialization, card issuance, card recovery, card recharge and other services; the daily operation and maintenance operations of the card system operation and maintenance personnel include a card terminal equipment Registration, access, transaction correction, card warehouse processing, accounting problem processing. Business operations involve key security factors such as keys and card structure information. Need to ensure the safety of your work computer. Business docking security: One card is based on its identity recognition function. More business considers the entry of a card as an identity. In this paper, the business docking security refers to the card system, which can realize the interconnection information communication with the third-party system and ensure the security of data and system. Different services, different docking methods, such as opening a certain key and structure of the card, providing a database access interface, providing a data interface in the form of WebService. When a card is docked with a third party, the card's core service information and data will inevitably be provided to third parties to varying degrees, increasing the security risk of the card. Operating angle: 7×24 uninterrupted operation The card system not only has some offline POS machines, but also real-time online applications, such as attendance, registration and other application systems, student power purchase systems, self-service recharge and so on. If the card operation is interrupted, the online business will be interrupted, which will directly affect the students' purchase, recharge and self-service card services, which will affect the lives of teachers and students. In some colleges and universities, there was a case in which a card could not purchase electricity, which led to a big wave caused by the lack of electricity in the dormitory. One-card server security is the foundation of system security and is a very important security factor among all factors. Server security mainly includes: server hardware device operation security, server operating system security, core database security, and so on. Server stability is related to the strategy of building a server. For example, whether to use hot standby, whether to use high availability, the backup and recovery mechanism of the database, and the stability of the application background are directly related to the operation security of the card system. Smart card system angle The smart card system itself is also a very important security factor. At present, many colleges and universities still use the M1 card. The M1 is a contactless logical encryption card. The key is a preset fixed password, which is stored in the card sector and can be easily copied. As early as October 2008, the method of cracking the password of MIFARE CLASSIC IC chip was announced on the Internet. By using this method, criminals can illegally recharge or copy all kinds of "one card" and access card using the chip at a low economic cost. , bringing great social security risks. For this problem, most colleges and universities upgrade the system, basically adopt the CPU card system. The CPU card breaks the mode of the original M1 card and is no longer sector storage. All applications are stored in the form of files, encrypted and stored in the card. The reading and writing of the files is realized by the response of the OS OS to the instructions in the card, which greatly improves the security of the card. In addition to the card itself, the tools associated with the M1 card are also an important factor in the safety of the card. The logical key system and POS device of the M1 card system lack an effective security authentication mechanism and can be forged. The CPU card encryption algorithm and the random number generator and the key authentication card (SAM card) installed in the reading and writing device can mutually authenticate: 1. Implement the authentication of the card through the SAM card on the terminal device. 2. Mutual authentication between the non-contact CPU card and the SAM card on the terminal device to implement authentication of the card terminal. 3. Recharge the non-contact CPU card through the ISAM card to achieve safe stored value. 4. The non-contact CPU card is devalued by the PSAM card to achieve safe deduction. The security is enhanced, and the unsafe problem that one device of the original M1 card can be both devalued and added can be avoided. Regarding the security issue at this angle, the M1 card is replaced with a CPU card, which basically ensures the security of the card itself. Therefore, when upgrading or creating a new card system, selecting the CPU card system can avoid the security problem of the card itself. Financial rigor It is not a good idea to classify a card as a financial system. Every day, the consumption of teachers and students in the whole school will generate a large amount of consumption water. The system will flow the water every day, settle according to the merchants, and then generate financial statements. The card system has a complete set of financial mechanisms and financial processes. First, in this financial system, the security of transactions is a prerequisite security factor. The system must ensure that the transaction data is correct, complete, and cannot be tampered with or forged. In addition, there are inevitably certain abnormal situations in the transactions within the card system, such as illegal card consumption, loss of card consumption after the loss of a card, abnormal state of the card, illegal malicious large amount of money after the card is illegally held, etc. problem. These problems must be circumvented by corresponding mechanisms, such as: Two-way confirmation of card and device authenticity through digital signature and two-way authentication; The system realizes the security of transactions through black and white list management; Card status and expiration date identification function can effectively prevent expired cards from being used; The system also provides illegal card and black card alarm functions; large-scale consumption requires a password and other mechanisms. Secondly, the accuracy and integrity mechanism of financial statements is also an important factor in the financial security of the card. The system is created with the audit function in mind, the internal automatic reconciliation function, the automatic alarm function of the card library, etc., which can be found in multiple directions. safe question. Daily management perspective The daily management of the card system also involves more security issues. The daily management mainly includes: one-card staff management, one-card terminal equipment management, one-card system finance, accounting management, and system security use management. One-card staff management: One-card staff includes system administrators, system operation and maintenance personnel, card business personnel, etc. These three parts are the core strength to ensure the safe and stable operation of the card. The quality of team management determines whether the system can continue to be stable and benign. Running. For example, work discipline, normativeness of daily business operations, systemic confidentiality, etc., may directly and indirectly affect the safety of the card. One-card terminal equipment management: including hardware asset management, maintenance management, hardware access management, and so on. There are many types of terminal devices, and the campus is widely distributed and unattended. Therefore, property security of assets is also a big problem; equipment damage repair may result in loss of water in the equipment, resulting in accounting problems and loss of merchant turnover; hardware Access must be in accordance with the corresponding technical specifications, such as canteen POS equipment, water control POS machine, rigorous random transfer and random removal, etc., will lead to short circuit, burned equipment. The management of finance and accounting of the card system: There is a cash business in the card, and there must be a strict management system for the storage of cash receipts and payments. For example, there may be cash and accounting inconsistencies, unclear cash issues on the day, cash theft, security issues, cash operators' professional ethics and literacy issues, etc. These factors must be considered in the management system. Potential security risks. System security usage management: There are many card subsystems, and the system must have the function of hierarchical management to ensure the security of operations. Different levels of people have different menus and system privileges, and each business does not affect each other. At the same time, the system has a security audit function. The administrator avoids password leakage during system use and login, ensures that the system is used in a safe and non-toxic working environment, and prohibits arbitrary access to external USB devices. These are essential elements for system security, as shown in Figure 3. Data security perspective The card generates a lot of consumption data, attendance data, access control data, as well as data about basic personnel information. Most of the data involves personal privacy, and the data itself hides a lot of important information. The importance of data security is self-evident. Ensuring the confidentiality, integrity, and correctness of data is unquestionable. The use of data also involves some security factors: card account information and data sharing issues, data access transmission issues, data encryption mechanisms, data storage backup mechanisms. With the rise of the era of big data, data security is becoming more and more important. In summary, the security of the campus card system includes many aspects, some aspects are to be circumvented during the system construction period, and some aspects are controlled by strategies such as supervision and management in the future. One-card security is a comprehensive and comprehensive system engineering. All kinds of security policies must cooperate with each other. Organic coordination can really protect. Even so, the security issue is not once and for all. The absolutely safe strategy requires us to constantly explore and prevent problems before they happen. (The author unit is Shanghai Maritime University Information Office)
The lip brush is used to apply lipstick. Use a lip brushes or a lip liner to spread the lipstick better. The retractable lip brush is generally a flat tongue brush. After dipping the lipstick, outline the lip shape first, and then evenly fill in the color. Most girls are not used to applying lipstick with a best makeup lip brush, so they just apply it directly. This is easy to contaminate bacteria, and the poster will not be evenly silky. If you want to create a uniform lip color in the poster, you must use a best lip brush to apply it.Common lip brush:Lip Brush Retractable,Lip Brush Best,Best Lip Brush,Lip Brush Disposable,Makeup Lip Brush
Portable retractable lip Makeup Brush: special design and styling, retractable and automatic seal, clean and hygienic, no hair removal and easy to clean easy to use and portable; Can be put in a long wallet or cosmetic bag, good for carrying and traveling Lipstick Brush,Best Lip Brush,Lip Brushes,Makeup Lip Brush,Retractable Lip Brush,Best Lip Brush,Disposable Lip Brush,Lipstick Brushes Shenzhen Nanfang Shishang Cosmetic Utensil Co., Ltd. , https://www.sznfssmakeupbrush.com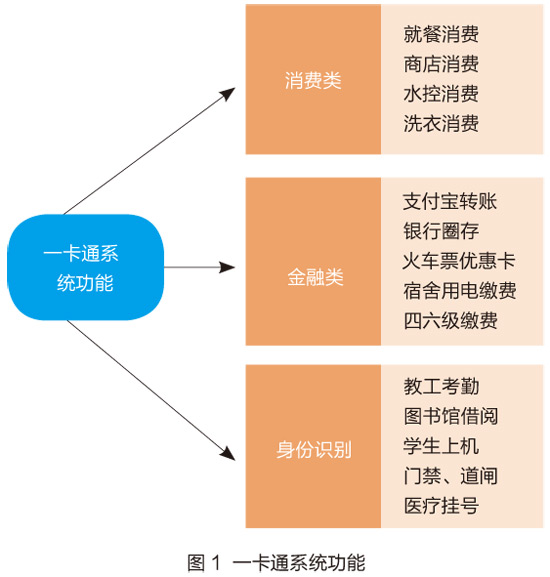
Give yourself a makeover: ample brush hair and flexible brush handle, color smooth and expert lip lines
Good material: super soft synthetic bristles is dense and fill lip or eye lid appropriately, can be applied as lip brush, eyeshadow brush, foundation Concealer Brush